
Kali Wifite Handshake Location Code
Aircrack is one of the most popular tools for WEP/WPA/WPA2 cracking. Hcxtools Description. Small set of tools convert packets from captures (h = hash, c = capture, convert and calculate candidates, x = different hashtypes) for the use with latest hashcat or John the Ripper.The tools are 100% compatible to hashcat. I'm using the latest builds of Kali Linux and I use the following command: wifite -pyrit -dict./rockyou.txt But after capturing a WPA Handshake, it says that no dictionary was found 00. To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. (^C) WPA handshake capture interrupted + 2 attacks completed: + 0/2 WPA attacks succeeded + quitting Now the deauth attacks weren't working. This time I increased the deauth frequency. Root@kali:# wifite -wpadt 1. Soon, however, I realized, that the problem was that I was using my internal card (Kali Live USB).
Previously, Kali Linux was introduced to you. It contains a large amount of Penetration Testing Tools. Today you will learn about one other tool of this collection. WiFite is a Penetration Testing Tool under the GNU General Public License version 2 and in this article, we will present How To Install And Run Wifite On Kali Linux. You can customize WiFite to be automated with only a few arguments and attack multiple Wired Equivalent Privacy, Wi-Fi Protected Access, and Wi-Fi Protected Setup encrypted networks in a row. It has been designed to use all these recent methods for retrieving the password of a wireless access router. Once you start running WiFite, you can select your targets, and then it will start capturing or cracking the password. You do not need to memorize command arguments and switches anymore, WiFite will run the existing wireless-auditing tools for you. You can find your preferred Linux VPS packages and continue learning how to use this tool on your own server.
Tutorial Install WiFite On Kali Linux
WiFite Features
1- WiFite is able to crack the closest access points due to their signal strength first while it sorts targets in dB.
2- De-authenticates clients of hidden networks automatically to reveal SSIDs.
3- It has so many filters to specify what to attack exactly.
4- Timeouts, packets/sec, and other settings are customizable.
5- WiFite can change MAC to a random address before the attack as an anonymous feature. When attacks are complete, change back.
6- It provides the backup of all captured WPA to wifite.py’s current directory.
7- It cycles between all clients and broadcast deauths as a smart WPA de-authentication.
8- You can easily stop the attacks with Ctrl+C and move onto the next target with options to continue or even skip to cracking and exit.
9- You can view the summary of the session at the exit and see the cracked keys.
10- You will find all saved passwords to cracked.txt
11- The built-in updater is available on ./wifite.py-upgrade
Required Tools
1- A wireless card with the ”Monitoring Mode” ability and packet injection.

2- The latest versions of some programs are supported which should be installed to let WiFite work well such as python, iwconfig, ifconfig, Aircrack-ng, airmon-ng, aircrack-ng, aireplay-ng, airodump-ng, packetforge-ng.
3- The suite of programs it uses, forces WiFite to be run as root. While it is not a good idea to run downloaded scripts as root, you can use the Kali Linux bootable Live SC, a bootable USB stick, or a virtual machine. In case you use a virtual machine you need to prepare a wireless USB dongle since they cannot access hardware directly.
Learn Install And Run WiFite On Kali Linux Step By Step
WiFite is designed for the latest version of Kali Linux. If you are using the latest version of the required tools, WiFite can support other pen-testing distributions like BackBox or Ubuntu Server. Now that you got familiar with WiFite enough, it is time to see how easy is to install it on Kali Linux.
How to Install WiFite On Kali Linux
Run the following command to install WiFite:
It will install the WiFite and all packages.
Also, you can install WiFite onto your computer (from any terminal) by running:
In this way, you have installed wifite to /user/bin/wifite which is in your terminal path.
Use the commands below to install dependencies:
Kali Wifite Handshake Location
How To Run WiFite On Kali Linux
Type the following command to run WiFite:
Screenshots
1- Cracking WPS PIN using reaver ‘s Pixie-Dust attack, then fetching WPA key using bully
2- Cracking WPA key using PMKID attack
3- Decloaking and cracking a hidden access point
4- Cracking a weak WEP password
5- Cracking a pre-captured handshake using John The Ripper
How To Uninstall WiFite From Kali Linux

If you decide to uninstall WiFite, you need to record the files which you have installed by the above command in the installing part and remove those files:
If you wish to use pip install instead of python setup.py install, remove all files and undo any other stuff that installation did manually. But if you do not know the list of all files, record a list of installed files. Type the command below to do this:
And then, use xargs to do the removal when you want to uninstall:
That’s that! By reaching this point you have read a brief introduction to WiFite, the way of installing, running, and remove it. Feel free to buy your preferred VPS and then we are beside you to learn how to install and configure Kali Linux on it.

Conclusion
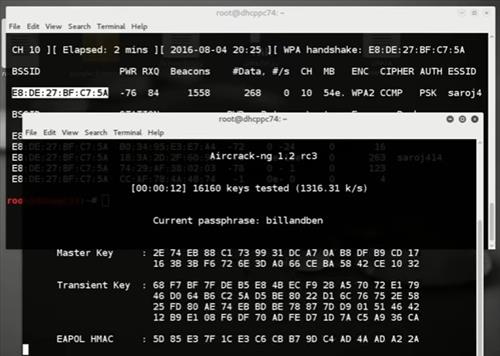
In this article, you learned How To Install And Run WiFite On Kali Linux. In February 2011, the New York Times called the WiFite as the ”New Hacking Tools Pose Bigger Threats to Wi-Fi users”. Now fewer bugs are being detected as well as it does not leave processes running in the background while it was an issue in the previous versions. Enjoy the speed and accuracy of this tool and reach your considered purposes. In case you are interested in reading more, find our related article on How To Install Nishang On Kali Linux.